In today's ever-evolving digital landscape, the need for seamless integration between Microsoft SharePoint, Microsoft Teams, and 3rd party applications has become paramount. This integration plays a vital role in fostering efficient collaboration and enhancing overall productivity. However, we cannot overlook the challenges that arise when it comes to ensuring the security and compliance of these integrations.
As the Microsoft 365 landscape continues to evolve, with the introduction of developments like Copilot and other AI tool, it has become even more crucial to address concerns such as oversharing and data security. In this blog, I aim to shed light on these pressing topics and provide valuable insights based on my own experiences.
With the availability of multiple options for implementing integrations and collaboration between 3rd party applications and Microsoft 365, it is essential to choose the best method for your specific implementation. By carefully considering the security and compliance aspects, we can ensure that our solutions not only meet our business needs but also adhere to industry standards and regulations
Undersetting about Authentication and authorization
Authentication and authorization are critical when it comes to calling Microsoft Graph. Your application should first generate an access token from the Microsoft identity platform. Access tokens will contain information allowing to validate the caller and to ensure that the caller has proper permissions to perform the operation requested. There are different types of permissions, including application and delegated, and you should choose the most suitable approach for your needs.
There are three methods to integrate with SharePoint using Graph API.
For all other scenarios and details, you can visit Graph documentation.
Comparison of delegated and application permissions
| Delegated permissions | Application permissions | |
|---|---|---|
| Types of apps | Web app / Mobile / Single-page app (SPA) | Web / Daemon |
| Access context | Get access on behalf of a user | Get access without a user |
| Who can consent | Users can consent for their data Admins can consent for all users | Only admin can consent |
| Other names | Scopes OAuth2 permissions | App roles App-only permissions Direct access permissions |
| Result of consent | oAuth2PermissionGrant | appRoleAssignment |
| Supported signInAudience types Description Scenario Advantages | AzureADMyOrg AzureADMultipleOrgs AzureADandPersonalMicrosoftAccount PersonalMicrosoftAccount The app acts on behalf of the signed- in user and can access the same resources and perform the same operations as the user A web app that allows users to view and edit their own SharePoint documents The app can provide a personalized and interactive user experience. Data access only where user have permissions (ex, Delve or copiloit) | AzureADMyOrg AzureADMultipleOrgs AzureADandPersonalMicrosoftAccount The app acts on its own without a signed-in user and can access resources and perform operations based on the app roles A background service that performs automated tasks on SharePoint data he app can access data without user intervention and consent |
Sites.readAll or readWriteAll permissions. This method is not recommended as it grants highly privileged permissions to a service principal, meaning a service principal could literally read any site on your tenant. This approach poses a high risk of data leakage if the client ID and secret leak, as a hacker could read complete tenant data without knowing users and the organization.
Method 2: Site Collection Level 'granular' Permissions -with Application
Risk level: Low Medium
Update : MS Document SharePoint now supports delegated Sites.Selected authentication (microsoft.com)
Risk level: Low
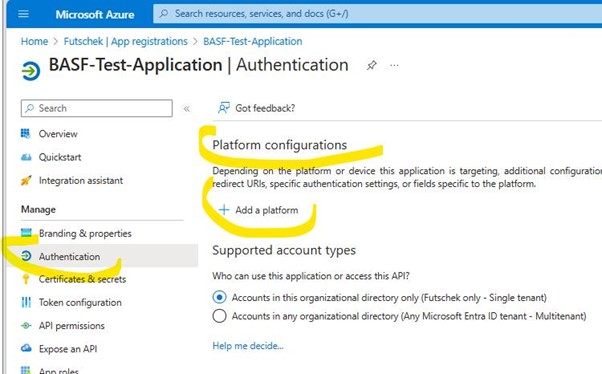
Within the app registration, you will find the topic
"Authentication" in the Menu on the left side (under
"Manage"):
At the very top you will find the platform configurations. Click on
"Add a platform"
Choose the application platform (depends on the application. In my test I
chose "Web"):
In the configuration tab, enter the respective infos (in my scenario the
redirect URI for the authentication responses --> tokens) and also select,
the types of tokens to allow (so access tokens, ID tokens or both). Hit
Configure to submit.
Now you need to adopt the following link:
https://login.microsoftonline.com/{tenant
id}/oauth2/v2.0/authorize?client_id={app-id}&response_type=token&scope=https%3A//graph.microsoft.com/Sites.Selected
Note : Change the {tenant id} and the {app-id} with your tenant ID (can be found at the main page of Entra in the Azure portal) and your application ID (can be found on the main page of your app-registration).
Sample : https://login.microsoftonline.com/9d66ab4f-475c-4fd6-a9a0-2613da2f5833/oauth2/v2.0/authorize?client_id=f4b3d77b-8c0d-419b-ada0-ac97ffedc9d1&response_type=token&scope=https%3A//graph.microsoft.com/Sites.Selected
You will be prompted for the application permissions. Check if the
application name is correct, then tick the box for "Consent on behalf opf
your organization" and click "Accept".
Reference :
https://learn.microsoft.com/en-us/graph/api/site-post-permissions?view=graph-rest-1.0&tabs=csharp
https://learn.microsoft.com/en-us/graph/permissions-overview?tabs=http
Conclusion:
In conclusion, integrating 3rd party applications with SharePoint using Graph API requires careful planning and consideration of security risks. By choosing the appropriate method and following the recommended steps, you can ensure that your sensitive data and resources remain secure and compliant.